AMD's Firmware-Based TPM Vulnerable to New Exploit
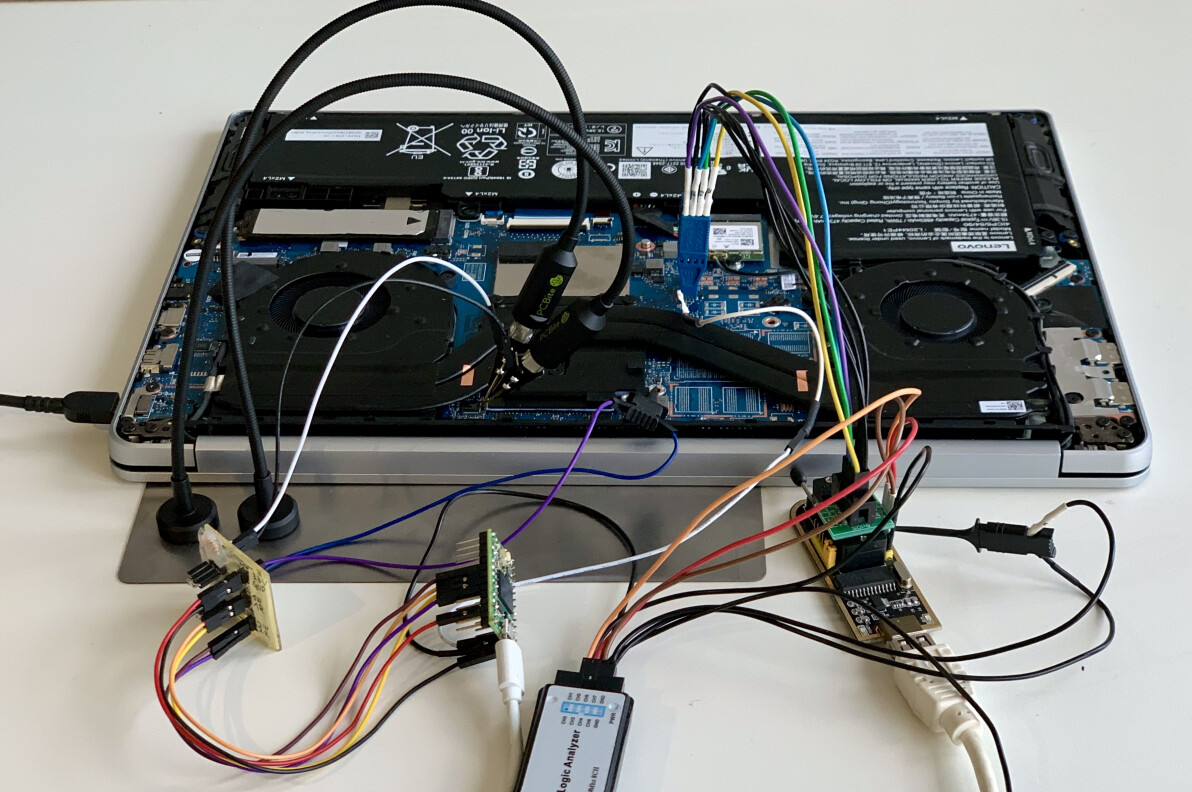
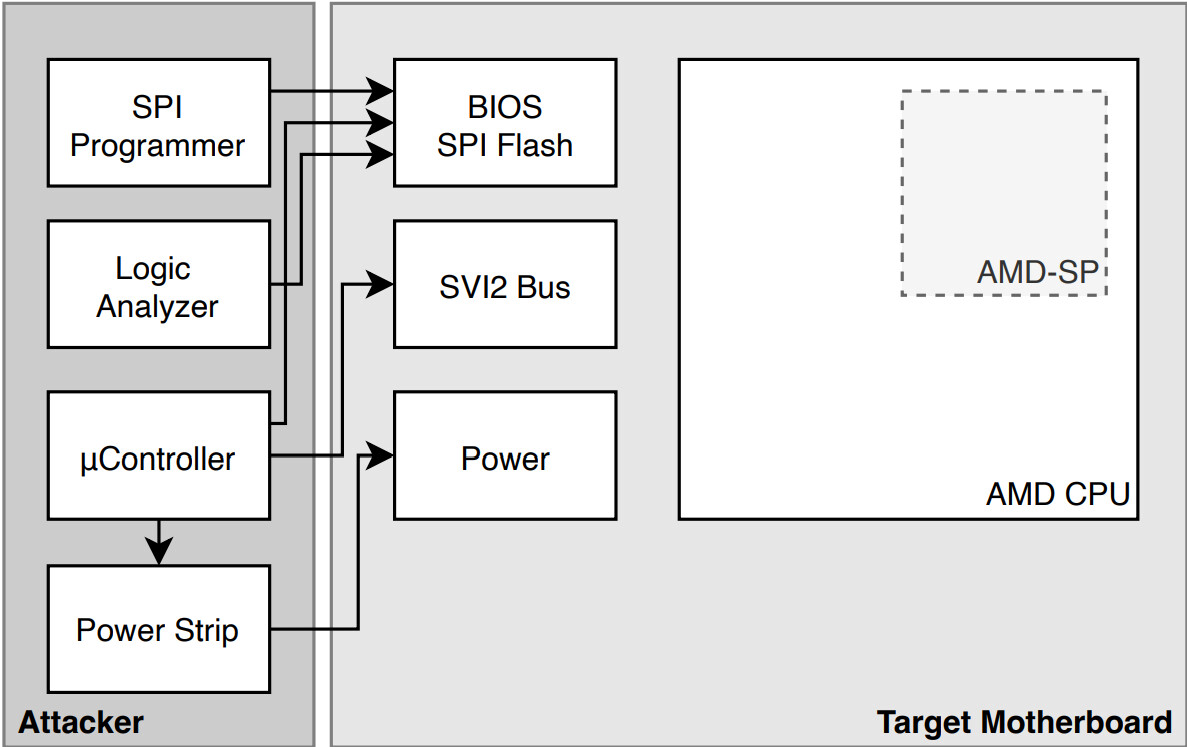
Researchers at the Technical University of Berlin have published a paper titled "faulTPM: Exposing AMD fTPMs' Deepest Secrets," which highlights a vulnerability in AMD's firmware-based Trusted Platform Module (TPM) that can be exploited by attackers targeting Zen 2 and Zen 3 processors. The faulTPM attack involves using the AMD secure processor's (SP) vulnerability to voltage fault injection attacks, which allows the attacker to extract a chip-unique secret from the targeted CPU. This secret is then used to derive the storage and integrity keys that protect the fTPM's non-volatile data stored on the BIOS flash chip.
The attack consists of two phases: a manual parameter determination phase and a brute-force search for a final delay parameter. The first step requires around 30 minutes of manual attention, but it can potentially be automated. The second phase consists of repeated attack attempts to search for the last-to-be-determined parameter and execute the attack's payload.
Once these steps are completed, the attacker can extract any cryptographic material stored or sealed by the fTPM regardless of authentication mechanisms, such as Platform Configuration Register (PCR) validation or passphrases with anti-hammering protection. BitLocker, which uses TPM as a security measure, is compromised by faulTPM.
Researchers suggest that Zen 2 and Zen 3 CPUs are vulnerable, while Zen 4 wasn't mentioned. The attack requires several hours of physical access, so remote vulnerabilities are not a problem. AMD has issued a statement acknowledging the vulnerability and is working on new hardware-based protections in future products to limit the efficacy of these techniques. The attack is also public with code available on GitHub.

Image source: Tom's Hardware